-
I recently stumbled across a practical use-case for simulated exceptions in C while writing a recursive-descent JSON
parser for fun and profit. In this quick write-up, I’ll give a high-level overview of the problems that I ran into, why
exceptions were ideal for error handling, and how I emulated them in C.
-
RSA is a public-key, or asymmetric, encryption algorithm.
In contrast to symmetric algorithms, like DES and
AES, which use the same key for both encryption and
decryption, RSA employs two distinct keys: a public key used to encrypt data, and a private key used to
decrypt whatever was encrypted with the public one. The beauty of public-key encryption is that the parties involved
never need to exchange a master key, meaning that communications can be securely encrypted without any prior contact.
-
Nand2Tetris, or The Elements of Computing Systems, is a twelve-part course in
fundamental computer engineering that steps you through the creation of a computer from the ground up, starting with
NAND logic gates and ending with an operating system capable of running a complicated program like Tetris.
-
Prime number spirals are visualizations of the distribution of prime numbers that underscore their frequent occurrences
along certain polynomials. They’re conceptually simple, yet create order out of the apparent chaos of primes and are
fairly beautiful. We’ll explore the Ulam and Sacks spirals, some of their underlying theory,
and algorithms to render each.
-
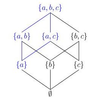
The power set of a set is the set of all its subsets, or a collection of all the different combinations of items
contained in that given set: in this write-up, we’ll briefly explore the math behind power sets, and derive and compare
three different algorithms used to generate them.